How to manually clean the wp-cleansong virus that comes with the Wordpress Litespeed Cache plugin? [SOLVED]
![How to manually clean the wp-cleansong virus that comes with the Wordpress Litespeed Cache plugin? [SOLVED] How to manually clean the wp-cleansong virus that comes with the Wordpress Litespeed Cache plugin? [SOLVED]](https://www.ajansfeedback.com/uploads/wpcleansong.jpg)
How to manually clean the wp-cleansong virus that comes with the Wordpress Litespeed Cache plugin? [SOLVED]
Information on wp-cleansong malware
A new vulnerability in the plugin Litespeed cache led to the detection of malware on websites and the suspension of Google ads. In this article, we will explain malware detection and manual removal. No security plugins are needed for wp-cleansong cleaning.
The Litespeed Cache plugin, which was updated in February 2024, caused malware to infect your site before and after the update. More than 4 million websites were affected and left vulnerable. Because of this vulnerability, hackers can compromise sensitive data and modify site content by installing malicious scripts.
Wp-cleansong malware detection
This malware can be detected by several malware. These are Wordfence and Sucuri. You can detect the virus by installing these two plugins on your WordPress website. However, if you want to remove the virus with these plug-ins, you will need to purchase the professional plans of the plug-ins.
We will explain to you how to get rid of the virus by manual cleaning method without using these add-ons.
How to perform wp-cleansong malware manual removal?
First of all, this plugin will create 2 users on your website. One of these users is an administrator and the other is a standard user.
Step 1
Get rid of these users.
Dashboard -> Users -> All Users
Go to page and delete all administrator accounts except your administrator account. Remember: Wp-cleansong will only create one user and one admin user.
Step 2
View your website's source code. You will see this in the source code:
(function(_0x3a4aa1,_0x45511f){function _0x4c0a9d(_0x2c492e,_0x22928f,….
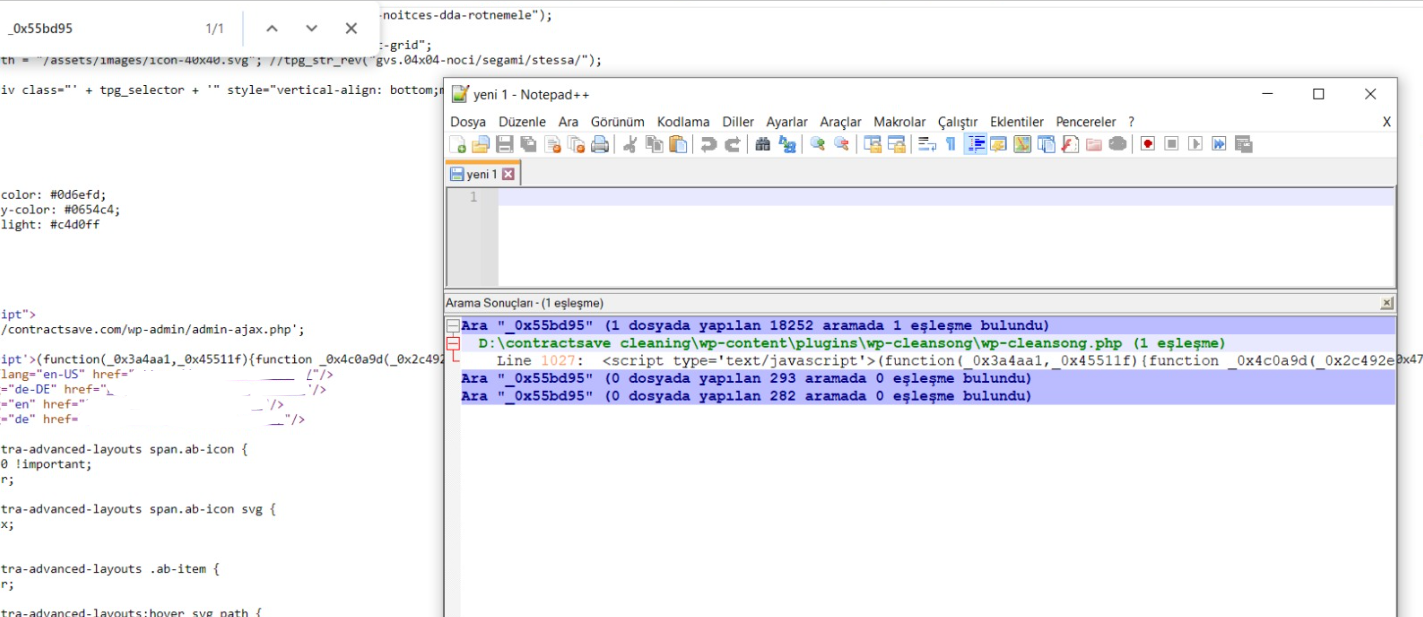
This code snippet is the code snippet created by Wp-cleansong. To clear this code, from your website files;
Wp-content -> plugins -> wp-cleansong
Remove the file.
This file will add another code snippet to the head section of your website. Removing the plugin will not delete this code snippet! Continue following the steps.
You will not see this plugin on the plugins page in your WordPress Dashboard. To remove the plugin, access the files using FTP or WP File Manager plugin.
Step 3
When you run the malware scan again, you will see that the malware is not gone from your site.
What you need to do now is to clean up the second code that the malware injected into your site.
View your website source code.
Search for: dmFyIHN0PWRvY3VtZW50LmNyZWF0
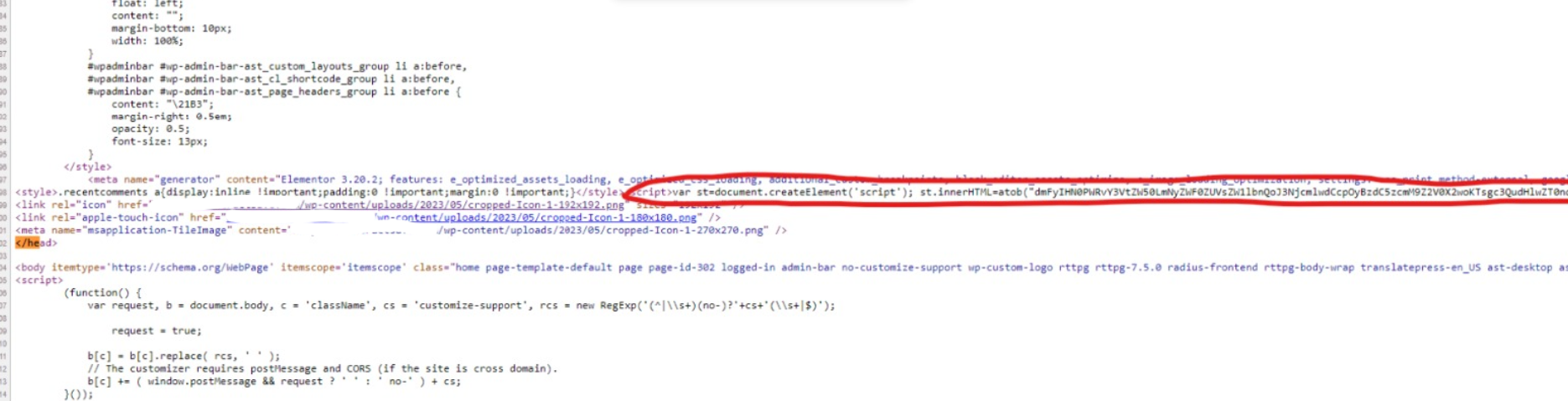
Here's where you need to clean up this snippet;
Download the wp-blog-header.php file in your website's main directory and open it with a code editor, or use the Wp File Manager plugin for this process.
You will see the code as follows;
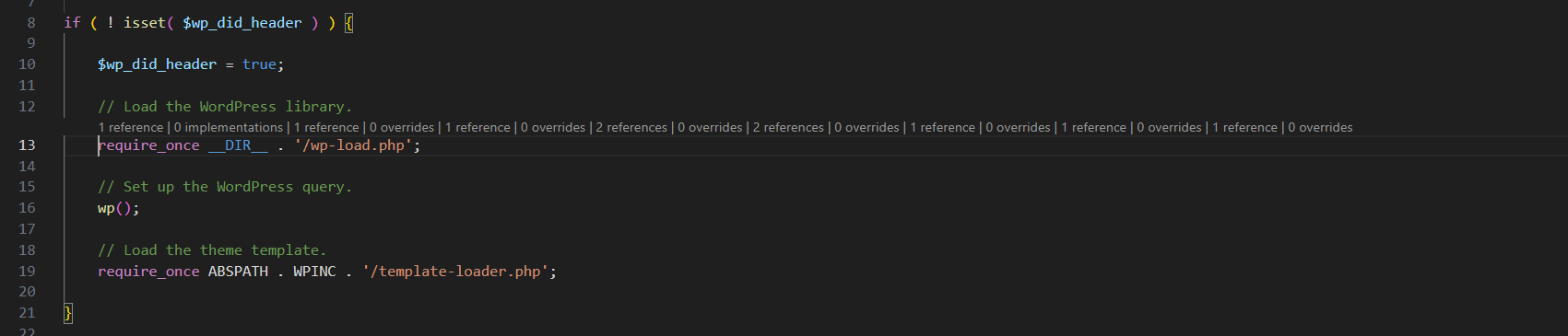
You need to clean up the reference code snippet here. You can use Notepad++ or VScode programs for this process.
Another method is as follows: Download a clean WordPress site source code and replace wp-blog-header.php with the one in the clean source code.
When you scan again, you will see that the malware has been completely removed from your site.
Information about the Flaw in the LiteSpeed Plugin
Implementation of shortcode functionality was the origin of the LiteSpeed plugin vulnerability. Without adequate data sanitization and evasion measures, this functionality gave hackers the ability to install malicious scripts. It is worth noting that this vulnerability is more difficult to exploit than unauthenticated threats because an attack would require the hacker to have participant-level permissions.
Once the code is injected into a post or page, it will run automatically whenever that page is accessed. This makes a wide range of malicious activities possible, such as theft of sensitive data, manipulation of site content, injection of administrative users, editing of files, and redirection of users to malicious websites.
Information About Affected Versions and Fixes
Versions 5.6 and earlier of the LiteSpeed Cache plugin are susceptible to an XSS attack. The latest version of the plugin, 5.7, was released on October 10, 2023; Updating is important for website security. If you do not keep it updated, the security of your site will be at risk.





